Sha Hash Cracker
Sha Hash Cracker' title='Sha Hash Cracker' />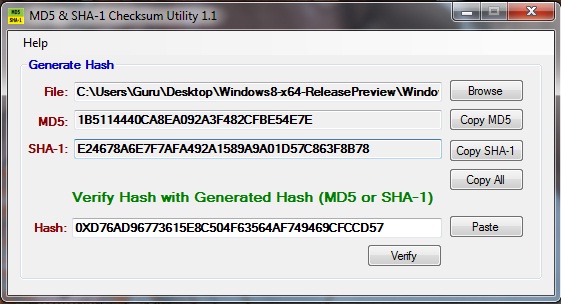 Best way to store password in database. Background. You never. You just want to verify an incoming user knows the password for an account. Hash It. Store user passwords hashed one way encryption via a strong hash function. A search for c encrypt passwords gives a load of examples. Whether you are a Hacker, Cracker or a Researcher, you need to face a number of hash strings in your day to day life. Hashing is a one way encryption of a plain text. Testing Injection. False means the query is invalid MySQL errorsmissing content on website True means the query is valid content is displayed as usual. See the online SHA1 hash creator for an idea of what a hash function produces But dont use SHA1 as a hash function, use something stronger such as SHA2. Now, a hashed passwords means that you and database thieves shouldnt be able to reverse that hash back into the original password. How to use it. But, you say, how do I use this mashed up password stored in the databaseWhen the user logs in, theyll hand you the username and the password in its original text. You just use the same hash code to hash that typed in password to get the stored version. AgoYkBxj8Y/Uecka_YTAUI/AAAAAAAAAyI/GxVTV8DzNgM/s1600/hashconsole_mainscreen_big.jpg' alt='Sha Hash Cracker' title='Sha Hash Cracker' />
Best way to store password in database. Background. You never. You just want to verify an incoming user knows the password for an account. Hash It. Store user passwords hashed one way encryption via a strong hash function. A search for c encrypt passwords gives a load of examples. Whether you are a Hacker, Cracker or a Researcher, you need to face a number of hash strings in your day to day life. Hashing is a one way encryption of a plain text. Testing Injection. False means the query is invalid MySQL errorsmissing content on website True means the query is valid content is displayed as usual. See the online SHA1 hash creator for an idea of what a hash function produces But dont use SHA1 as a hash function, use something stronger such as SHA2. Now, a hashed passwords means that you and database thieves shouldnt be able to reverse that hash back into the original password. How to use it. But, you say, how do I use this mashed up password stored in the databaseWhen the user logs in, theyll hand you the username and the password in its original text. You just use the same hash code to hash that typed in password to get the stored version. AgoYkBxj8Y/Uecka_YTAUI/AAAAAAAAAyI/GxVTV8DzNgM/s1600/hashconsole_mainscreen_big.jpg' alt='Sha Hash Cracker' title='Sha Hash Cracker' />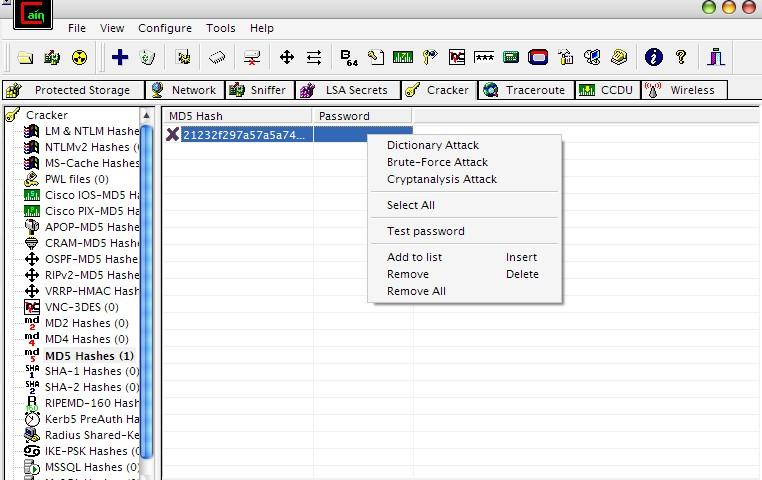 So, compare the two hashed passwords database hash for username and the typed in hashed password. You can tell if what they typed in matched what the original user entered for their password by comparing their hashes. Extra credit Question If I had your database, then couldnt I just take a cracker like John the Ripper and start making hashes until I find matches to your stored, hashed passwordsOxid. Cain Abel v4. 9. 56 released Added Windows Vault Password Decoder. Md51285123216. Cracker un mot de passe est malheureusement plus simple que ce que vous pensez. Voici la liste de 10 outils pour se faire la main. Answer Yes. yes they can. Windows 7 Loader 2.2 1 By Daz on this page. So, you should salt your passwords. See the Wikipedia article on salt. See How to hash data with salt C example. Coptic Fonts. MD5 Wikipedia. MD5 Message Digest Algorithm 51. MD52. IPv. 61. MD5MD4MD4MITRSA Ronald Linn RivestLinux md. Free. BSD md. 5 d. MD5MD5MD5RSAMD5MD5MD5MD5CRCCRC MD5MD5MD5MD5Free. BSDCDMD5MD5CD 5. RELEASE i. CHECKSUM. MD5 MD5MD5md. RELEASE i. 38. 6 miniinst. MD5 5. 1 RELEASE i. CHECKSUM. MD5. CHECKSUM. MD5. MD5 5. RELEASE i. MD5 5. 1 RELEASE i. MD5 5. 1 RELEASE i. MD5RIPEMD2. CRYPTO MD5MD5MD52. MD5MD5Secure Hash Algorithm SHA CRYPTRECMD5SHA 2. MD5 1. SHA 0SHA 1MD52D1D21D1D2D3HHD4D3HintegrityintegrityIntegrityAPOP2. IPAAPOP34APOPMD5SSLFlame2. FlameMicrosoft UpdateMD5MD5 5 Sophos 6Certificate AuthenticityFlame MD5 Windows Vista MD5 72. Certificate Authenticity8. FIGURE 1 Three types of cryptography secret key, public key, and hash function. Portable Powerpoint Viewer 2007 Free Download'>Portable Powerpoint Viewer 2007 Free Download. Learn about the best hacker tools, such as WikTo for Google hacking, password crackers, decoders and breakers, such as Cain and Abel and WLAN detectors. MD51MD56. F11MiKi3. MD51. MD53. ABCD 1. MD51F2. F4FB,C,DBCBDdisplaystyle FB,C,DBwedge Cvee neg Bwedge DGB,C,DBDCDdisplaystyle GB,C,DBwedge Dvee Cwedge neg DHB,C,DBCDdisplaystyle HB,C,DBoplus Coplus DIB,C,DCBDdisplaystyle IB,C,DCoplus Bvee neg D,,displaystyle oplus ,wedge ,vee ,neg XORANDORNOTMD5 3. K. s. Kfor i from 0 to 6. Ki floorabssini 1 2 pow 3. K. K 0. 3 0xd. K 4. K 8. 1. 1 0x. K1. K1. 6. 1. 9 0xf. K2. 0. 2. 3 0xd. K2. 4. 2. 7 0x. K2. K3. 2. 3. 5 0xfffa. K3. 6. 3. 9 0xa. K4. 0. 4. 3 0x. K4. K4. 8. 5. 1 0xf. K5. 2. 5. 5 0x. K5. K6. 0. 6. 3 0xf. ABCDvarint a. Avarint b. Bvarint c. 0 0x. Cvarint d. 0 0x. D 1append 1 bit to message. Mj, 0 j 1. 5. A a. B b. C c. 0. varint D d. F B and C or not B and D. F D and B or not D and C. F B xor C xor D. F C xor B or not D. Temp D. B B leftrotateA F Ki Mg, si. A d. Temp. end for. A. b. 0 b. 0 B. C. D. RFC 1. 32. 1 NANDAND. F D xor B and C xor D. F C xor D and B xor C. R. Rivest, The MD5 Message Digest Algorithm, RFC 1. April 1. 99. 2. Hans Dobbertin, The Status of MD5 After a Recent Attack, Crypto. Bytes Volume 2, Number 2, pp. Summer 1. 99. 6. 1Xiaoyun Wang, Dengguo Feng, Xuejia Lai, Hongbo Yu, Collisions for Hash Functions MD4, MD5, HAVAL 1. RIPEMD, IACR e. Print 1. Augst 1. 7 2. 00. RFC 1. 32. 1, section 3. Step 4. Process Message in 1. Word Blocks, page 5. Tao Xie and Dengguo Feng 3. May 2. 00. 9. How To Find Weak Input Differences For MD5 Collision Attacks. IPA APOP Software Integrity Checksum and Code Signing VulnerabilityMSFlame WUFlame malware used man in the middle attack against Windows UpdateFlame malware collision attack explained 2. RFC 1. 32. 1, section 2, Terminology and Notation, Page 2.
So, compare the two hashed passwords database hash for username and the typed in hashed password. You can tell if what they typed in matched what the original user entered for their password by comparing their hashes. Extra credit Question If I had your database, then couldnt I just take a cracker like John the Ripper and start making hashes until I find matches to your stored, hashed passwordsOxid. Cain Abel v4. 9. 56 released Added Windows Vault Password Decoder. Md51285123216. Cracker un mot de passe est malheureusement plus simple que ce que vous pensez. Voici la liste de 10 outils pour se faire la main. Answer Yes. yes they can. Windows 7 Loader 2.2 1 By Daz on this page. So, you should salt your passwords. See the Wikipedia article on salt. See How to hash data with salt C example. Coptic Fonts. MD5 Wikipedia. MD5 Message Digest Algorithm 51. MD52. IPv. 61. MD5MD4MD4MITRSA Ronald Linn RivestLinux md. Free. BSD md. 5 d. MD5MD5MD5RSAMD5MD5MD5MD5CRCCRC MD5MD5MD5MD5Free. BSDCDMD5MD5CD 5. RELEASE i. CHECKSUM. MD5 MD5MD5md. RELEASE i. 38. 6 miniinst. MD5 5. 1 RELEASE i. CHECKSUM. MD5. CHECKSUM. MD5. MD5 5. RELEASE i. MD5 5. 1 RELEASE i. MD5 5. 1 RELEASE i. MD5RIPEMD2. CRYPTO MD5MD5MD52. MD5MD5Secure Hash Algorithm SHA CRYPTRECMD5SHA 2. MD5 1. SHA 0SHA 1MD52D1D21D1D2D3HHD4D3HintegrityintegrityIntegrityAPOP2. IPAAPOP34APOPMD5SSLFlame2. FlameMicrosoft UpdateMD5MD5 5 Sophos 6Certificate AuthenticityFlame MD5 Windows Vista MD5 72. Certificate Authenticity8. FIGURE 1 Three types of cryptography secret key, public key, and hash function. Portable Powerpoint Viewer 2007 Free Download'>Portable Powerpoint Viewer 2007 Free Download. Learn about the best hacker tools, such as WikTo for Google hacking, password crackers, decoders and breakers, such as Cain and Abel and WLAN detectors. MD51MD56. F11MiKi3. MD51. MD53. ABCD 1. MD51F2. F4FB,C,DBCBDdisplaystyle FB,C,DBwedge Cvee neg Bwedge DGB,C,DBDCDdisplaystyle GB,C,DBwedge Dvee Cwedge neg DHB,C,DBCDdisplaystyle HB,C,DBoplus Coplus DIB,C,DCBDdisplaystyle IB,C,DCoplus Bvee neg D,,displaystyle oplus ,wedge ,vee ,neg XORANDORNOTMD5 3. K. s. Kfor i from 0 to 6. Ki floorabssini 1 2 pow 3. K. K 0. 3 0xd. K 4. K 8. 1. 1 0x. K1. K1. 6. 1. 9 0xf. K2. 0. 2. 3 0xd. K2. 4. 2. 7 0x. K2. K3. 2. 3. 5 0xfffa. K3. 6. 3. 9 0xa. K4. 0. 4. 3 0x. K4. K4. 8. 5. 1 0xf. K5. 2. 5. 5 0x. K5. K6. 0. 6. 3 0xf. ABCDvarint a. Avarint b. Bvarint c. 0 0x. Cvarint d. 0 0x. D 1append 1 bit to message. Mj, 0 j 1. 5. A a. B b. C c. 0. varint D d. F B and C or not B and D. F D and B or not D and C. F B xor C xor D. F C xor B or not D. Temp D. B B leftrotateA F Ki Mg, si. A d. Temp. end for. A. b. 0 b. 0 B. C. D. RFC 1. 32. 1 NANDAND. F D xor B and C xor D. F C xor D and B xor C. R. Rivest, The MD5 Message Digest Algorithm, RFC 1. April 1. 99. 2. Hans Dobbertin, The Status of MD5 After a Recent Attack, Crypto. Bytes Volume 2, Number 2, pp. Summer 1. 99. 6. 1Xiaoyun Wang, Dengguo Feng, Xuejia Lai, Hongbo Yu, Collisions for Hash Functions MD4, MD5, HAVAL 1. RIPEMD, IACR e. Print 1. Augst 1. 7 2. 00. RFC 1. 32. 1, section 3. Step 4. Process Message in 1. Word Blocks, page 5. Tao Xie and Dengguo Feng 3. May 2. 00. 9. How To Find Weak Input Differences For MD5 Collision Attacks. IPA APOP Software Integrity Checksum and Code Signing VulnerabilityMSFlame WUFlame malware used man in the middle attack against Windows UpdateFlame malware collision attack explained 2. RFC 1. 32. 1, section 2, Terminology and Notation, Page 2.